The following information is a little bit like the red pill in the Matrix: if you take it, you may not look at the internet in the same way and by finally knowing the truth, you can act accordingly. Knowledge is power, as they say.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
Please accept marketing-cookies to watch this video.
“If someone hacks my mobile or my computer, I really do not care. I’ve got nothing interesting on there. Besides, who could possibly be interested in coming after me?”
We’ve all heard and perhaps even said something similar to the statement above. Often we say something along these lines to justify that we do not have our antivirus software up-to-date, to excuse the fact that we don’t use secure passwords or because we connect to public Wi-Fi networks without any security.
Even more worrying is when people are not only unconcerned about their personal security and privacy but also are unbothered about what could potentially happen to their online business. A breach in this case could mean that you could not only have your personal data compromised but also that of all your clients, distributors and other partners. In addition, a website may have additional uses to a hacker.
“Fine, but why exactly would anyone hack me?”
That is exactly the point. It’s not that a hacker would directly target you for a specific reason. You after all, are just a regular person with nothing to hide. Although there are some exceptions where hackers carefully plan major attacks on large corporations, generally the great majority of hacks are random, perpetrated on websites that have minimum security and are vulnerable to attack, with the intention of entering and using the site as the hacker wishes.
This is a business that generates millions, it is no small matter. There are also cyber-attacks focused on political activism, corporate espionage, etc. But the most common type of hack you are likely to experience is one with a financial incentive.
How do they do it? Many times, hacks are initiated with innocent seeming actions like sending an email or a text message to thousands of people in the hope that some of them will open a link that appears inoffensive but actually grants the hackers access to your computer, tablet or mobile phone. For example, they might send a message that alleges you have won a prize, or maybe a notification from the post or a text from your bank. Sound familiar?
Another typical hack can occur when we connect to a public Wi-Fi network. We connect thinking that it is a secure environment, when in reality the hackers are impersonating that public network and we are in fact entering the hackers’ network.
Cloning a mobile SIM card is another easy way to hack a phone. Using an overly simple or obvious password is another door through which a hacker can enter. All of these situations are pretty common as we are often lax and do not take the necessary precautions.

“But I am a nobody! Why would they hack my website?”
As we’ve seen, it’s just business. Your website becomes a tool for the hacker who preys on it in order to monetize the site.
This can impact you in several ways: first, your server may be used to executive malware and store content that is not yours. A hacker may also take advantage of your online reputation, tainting your domain name for the foreseeable future and damaging your business long-term.
A Wordfence study highlights what are the most common uses are for hacked WordPress sites:
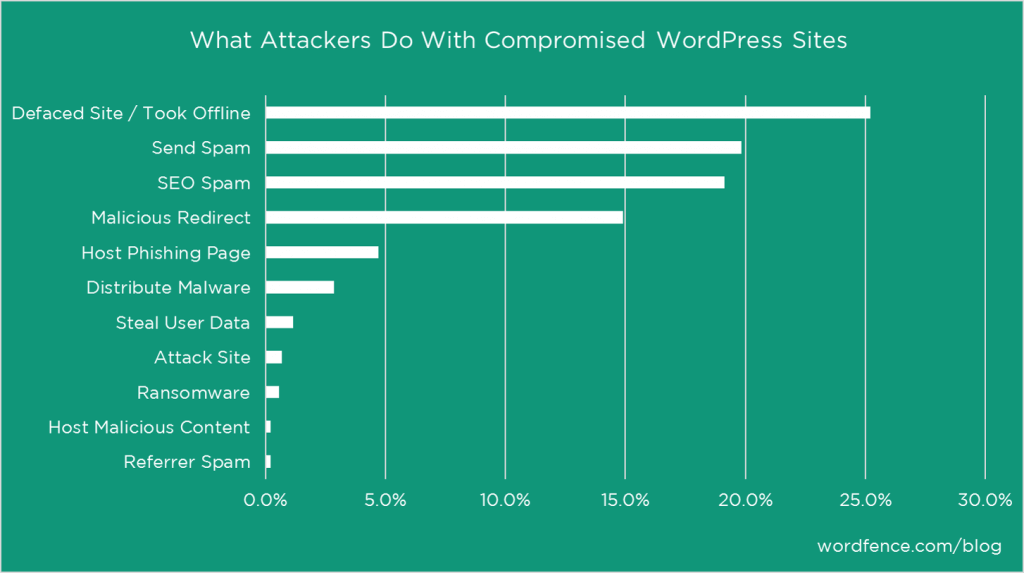
Common uses include:
- Replacing your content with their content (less common when there is an economic motive).
- Taking the site entirely offline (say to benefit one of your competitors)
- Sending spam for free from your web server
- Improve their rankings in Google whilst hurting your SEO by rerouting legitimate traffic to your site to other sites.
- Creating phishing pages to capture bank and credit card data, commit identity fraud or rob other valuable data.
- Demanding a ransom after they have taken over your web. In 2020 alone, over 3 billion ransomware attacks were registered.
“What should I do to protect my website?”
To stay safe from these types of internet fraud, check out our article on cyber-crime prevention which details steps you can take to protect your business’ security.
And just like Neo in the Matrix, the truth may not thrill you, but you can still join the resistance, protecting your website and your devices from prying hacker hands along the way.
Additional information
Staying Safe: The Wordfence Cyber Security Survival Guide from Wordfence
How do I know if my site was hacked? from wev.dev